Logmanager radically simplifies the management of your IT systems
Our software is developed in the Czech Republic. We cooperate closely with our customers and partners who provide us with feedback that drives our roadmap and makes implementation of important functionalities much faster.
Náš nejnoější systém zvládne vše.
Read more →

Logmanager makes it easier to comply with legislative requirements

Everyone on your team can learn how to work with Logmanager
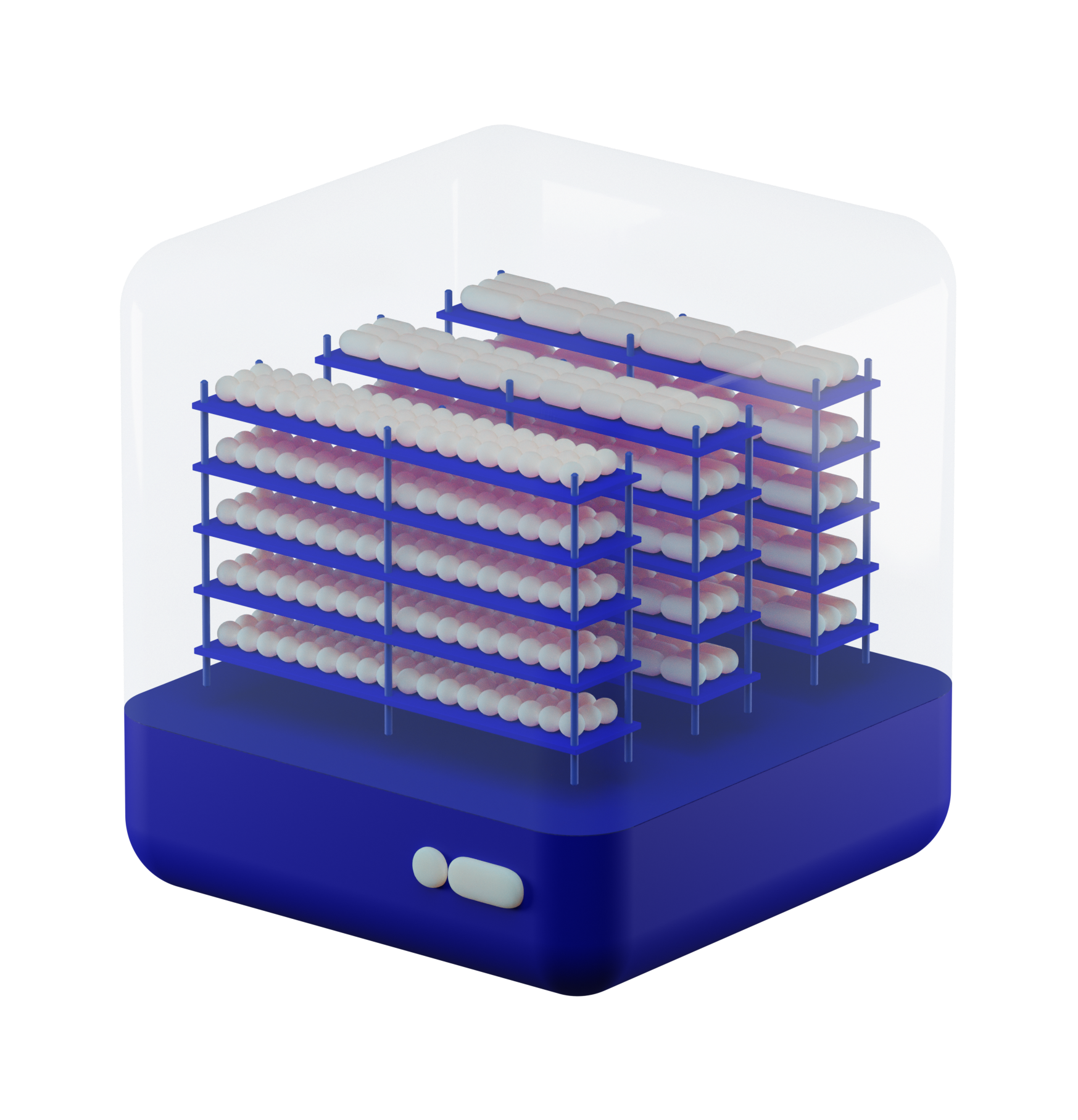
Our software is developed in the Czech Republic. We cooperate closely with our customers and partners who provide us with feedback that drives our roadmap and makes implementation of important functionalities much faster.
What's more, our tool offers scalability - as your business grows, Logmanager can adapt to your needs. Need more log processing power? No problem, simply switch to a bigger box or create a cluster.
I want to try Logmanager

Inquire Logmanager
Are you interested in trying Logmanager?
Do you want to do more than just collect events/incidents/logs?
We have a solution for you!
Thanks to our certified partners, we can lend you a Demo box in your IT environment that has all the same features as the full-fledged Logmanager and its open the door to radical simplicity not only in the field of log collection.
The Demo Box will allow you to get familiar with all the advanced features, make a basic estimate to select the right model, and gain network visibility at the same time.
Feel free to contact us, we'll be happy to arrange a demo and assist you with testing.

